File carving: Recovering a deleted file from a Windows disk image
Most computer users assume that when they delete a file and empty the Recycle Bin, it’s gone forever. After all, if Windows doesn’t show us a file, it doesn’t exist anymore, right? Wrong. With the right tools and knowledge, forensics experts can find fragments - or even complete versions - of deleted files that remain on the hard disk long after they disappear from Windows Explorer.
In this post, I’ll run through how to take a disk image and recover deleted files using FTK Imager and a hex editor, explain why this works, and show how certain utilities let you overwrite this remnant data.
What happens when you delete a file?
To give myself something to find, I created the text file shown below on a 2GB hard drive partition. I saved it, then closed it, deleted it, and emptied the Recycle Bin to render it inaccessible to any normal Windows user. But what is actually happening in the background when you do this?
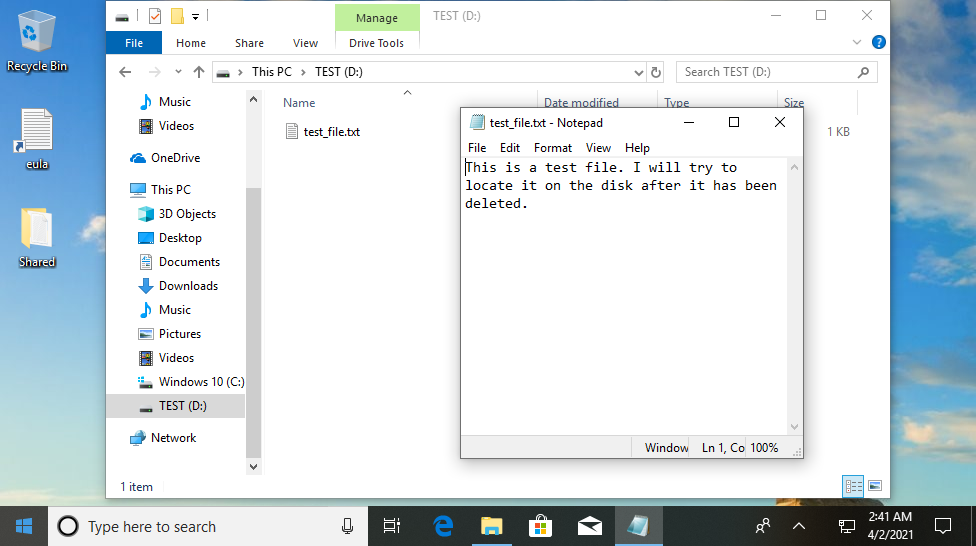
At the top of your hard drive is what’s known as the master file table (MFT). This is essentially an index - it contains filenames along with the addresses on the hard drive that these files can be found at. So when I create test_file.txt, an MFT record is created containing that filename and the address where the data (i.e. the file contents) is stored - in this case that’s 40009D50h, but we don’t know that yet.
When you delete a file, none of this information is removed from the disk. All deletion does is add a “deleted” flag to the MFT record, telling the computer that the information at the specified address is no longer needed and can be overwritten with new data if necessary - but nothing is actually deleted at this point and the file data is still present on the disk. You can probably guess where this is going…
Creating a disk image with FTK Imager
With the right tools, we can access the remnant data. First, we need a physical disk image to work with. FTK Imager is a free tool that allows us to create one. We choose a few simple options (I’m generating an image in the E01 format) and set it to work. Depending on the size of the disk and your computer’s speed, it will take a little while to generate the image, which is an exact replica of the hard drive.
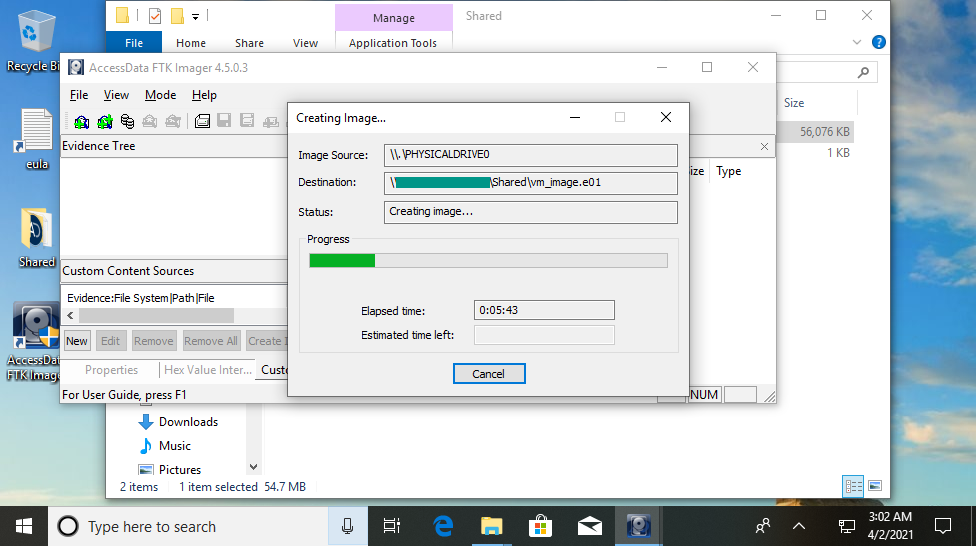
One thing to note is that the image cannot be generated on the same physical hard drive that is being imaged. For this reason, unless the system has multiple hard drives, it is necessary to choose to save the image to a directory on a removable drive or a network share, rather than on the subject computer itself.
Recovering a deleted file with FTK Imager
FTK Imager can also be useful for the next step in our process - it can actually do the hard work for us and recover the deleted file. If we mount the physical image we created and open the correct partition, we can navigate through the file system to find deleted files, which will be marked with a red cross.
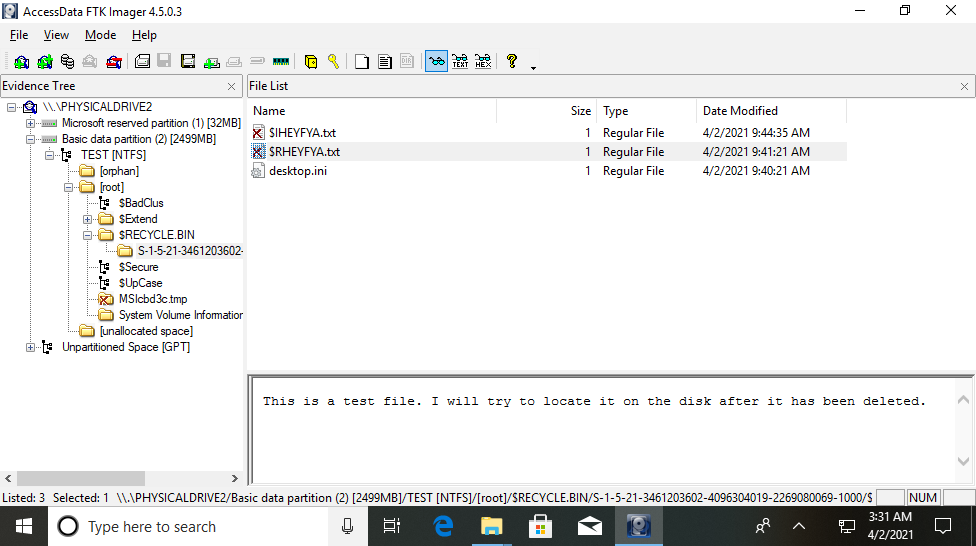
As the last place the file was present was the Recycle Bin (read my post about Python forensics for the Recycle Bin for more information about the file structure), its MFT entry points to that directory. Here, we can see that the file $RHEYFYA.txt is our test file, and FTK Imager helpfully displays the contents.
Recovering a deleted file with a hex editor
But things won’t always be that easy, and we shouldn’t rely on tools to do our forensics for us without knowing how they work. We can find the same data manually by mounting the disk image and opening it in a hex editor - in this example, 010 Editor. This displays the entire contents of the hard drive in hex format, and has a helpful feature that will search for strings amongst the data in the image.
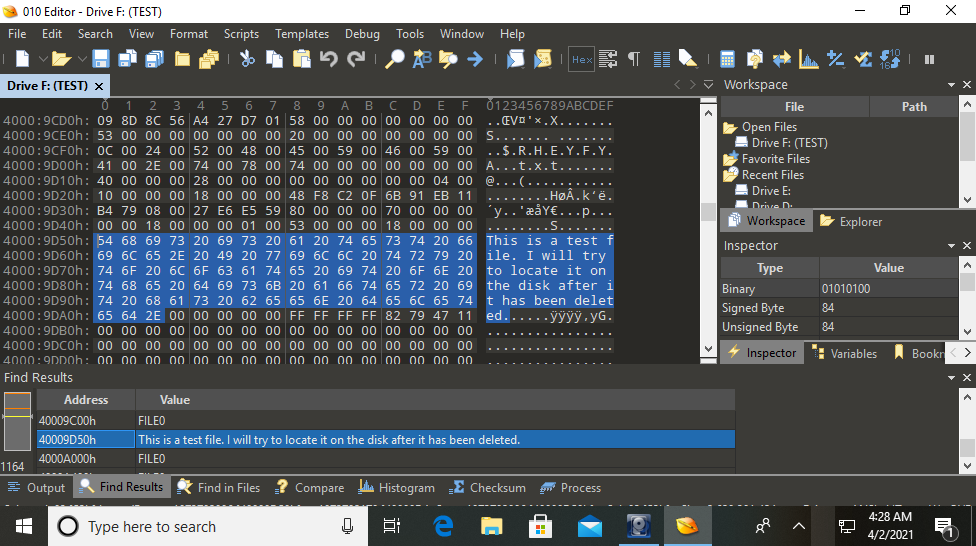
As you can see, I was able to find the text file’s contents by searching for strings. If we were looking for a different type of file, we might search according to its file signature, which indicates what format the file is in (for example, JPEGs start with FF D8 FF E0). Text files don’t normally have signatures, and in this case we can see the file data starts immediately at the address 40009D50h.
Overwriting traces of deleted files
So we’ve seen that it’s possible to recover deleted files, but is there any way to remove them from the disk completely? In short: yes, there is. Tools like CCleaner can overwrite the free space on a hard drive with nonsense data. If I run CCleaner’s Drive Wiper feature on our partition and repeat the above process, we can see that the address formerly occupied by test_file.txt is now full of zeroes.
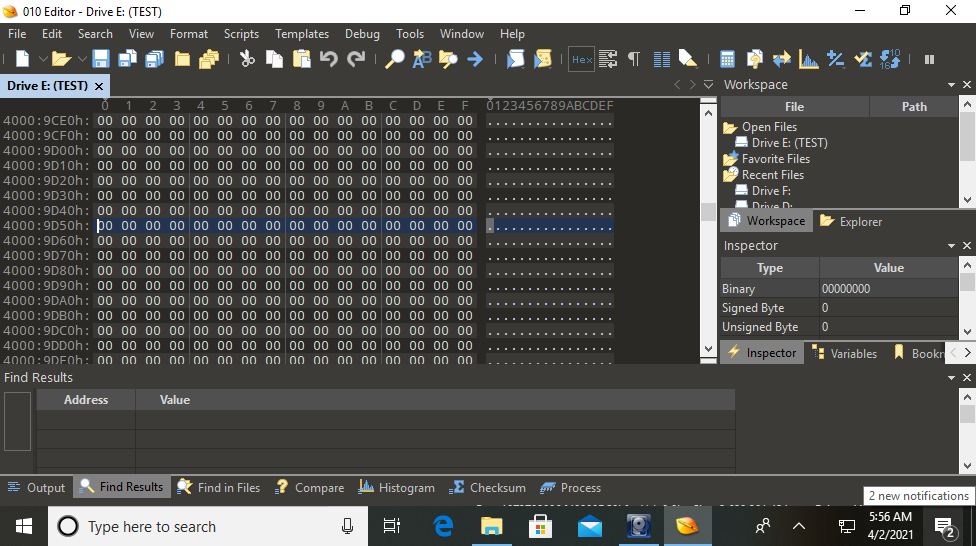
While this prevents a forensic investigator from recovering a file’s contents if done correctly, using some of these tools will arouse suspicion in itself. Some wipers will fill free space with ones, Zs, or random data, and this does not normally occur naturally. If this is observed on a hard drive then questions will be asked over whether the user was trying to hide something and a more thorough search may be conducted.

