Cracking a password-protected ZIP file with fcrackzip
I recently took part in a DFIR capture the flag with some colleagues. Participants were provided with a system disk image and asked to mount it and complete a number of challenges to discover various flags hidden within the data. Exercises like this are always both a lot of fun and a good way to share knowledge and learn - after all, there’s no better time to pick up new techniques than in the heat of competition.
I got most of the answers and finished joint second. One of the questions I didn’t have time for, which I deprioritised as I would have needed to look up the methodology, involved discovering the password to an encrypted ZIP file to access the flag inside. To make sure I can complete similar challenges in future CTFs (or live scenarios), I decided to do some digging, crack a ZIP, and document my method.
Creating a password-protected ZIP archive
To emulate the conditions of the CTF, I needed to create a ZIP archive containing a text file with the would-be flag. Creating the text file is a simple as using echo to write some content to a file.
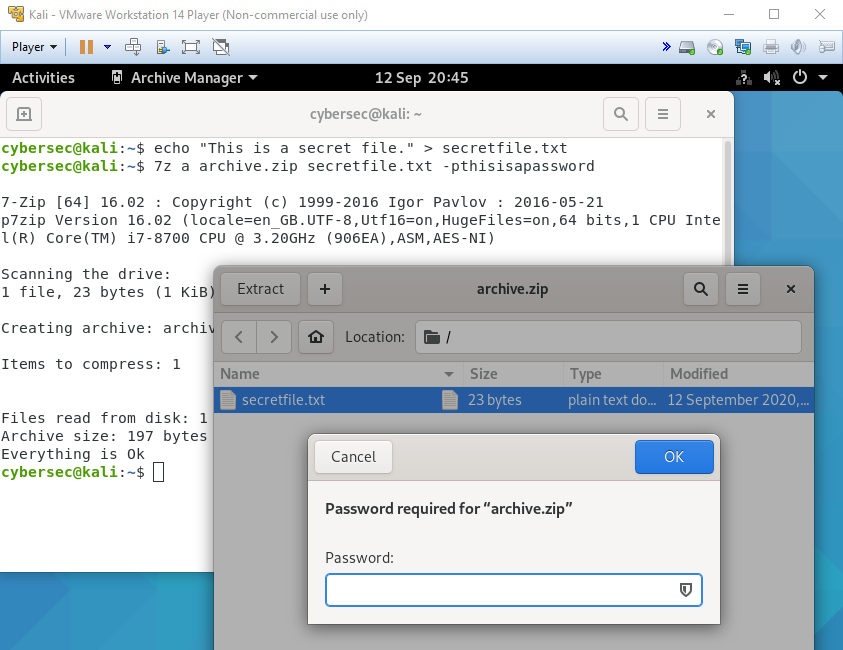
echo "This is a secret file." > secretfile.txtWe can then use 7-Zip to create a password-protected ZIP archive. The a option tells 7-Zip that we’re adding files to an archive. We then specify the name of the archive and the file we wish to add. Finally, the -p option allows us to add a password - in this case, the very secure thisisapassword. Also note that the lack of a space isn’t a typo - that’s just the way 7-Zip wants the information to be provided.
7z a archive.zip secretfile.txt -pthisisapasswordNow let’s check that the password was properly applied to the archive using the GUI. We can see that if we open archive.zip, we can see the file listing inside, but if we double-click to open any of the files we receive a prompt and cannot see the contents without entering the correct password.
Cracking the password-protected ZIP archive with fcrackzip
The tool we’ll use for discovering the password to our ZIP file is fcrackzip. We’ll use the -v option to generate verbose output and keep track of what it’s doing, and -u, which tells fcrackzip to attempt to use the guessed password to unzip the file to verify that it is correct and reduce the risk of false positives.
We have two options as to how fcrackzip will attempt to guess the password. Firstly, we can use the -b option to perform a brute force attack, guessing every possible combination of characters. This is useful for cracking long, unique passwords, but not the quickest method if you think the password may actually just be a simple combination of words, numbers, and symbols.
For these scenarios, we’d be better off performing a dictionary attack with -D. This guesses the password by trying every entry in a list of passwords. As such, fcrackzip requires you to provide a dictionary to use with -p. We’ll use the popular rockyou.txt dictionary - a mainstay of the cyber security profession.
fcrackzip -D -p rockyou.txt -v -u archive.zipWhen we hit return, fcrackzip will begin trying every password in the dictionary. When one of them successfully unzips the archive, it will stop and tell us what it is. The duration of this process depends on the dictionary, your computer’s processing power, and the password’s complexity, but in our case the password is so simple that we see results almost instantly.
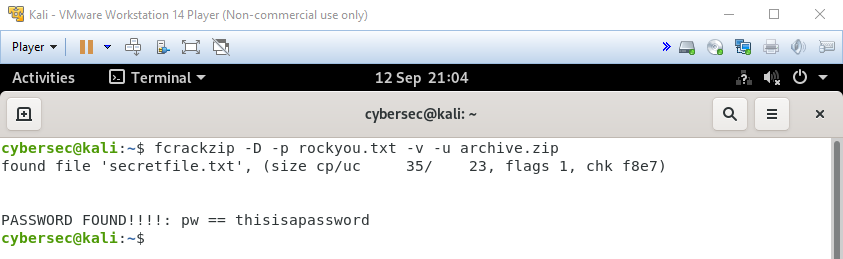
To view the contents of the archive, all we would have to do is copy the password from the output, open the ZIP file in the Linux GUI, and paste it into the password field when prompted. Then voilà - we’d have our flag, attacker-encrypted data, or any other files we were trying to access.

