Investigating external network connections with netstat and OSINT

When investigating a potentially compromised Windows computer, as well as looking at logs, files, and processes, it’s important to check its current network connections. Here’s how to retrieve that data with netstat and make sense of it.
Gathering data with netstat
First, open a Command Prompt window and use netstat to generate a list of the computer’s current network connections and send it to a text file. You can get this by entering:
netstat -n > connections.txtThe -n argument outputs the results as IP addresses, rather than trying to resolve them to hostnames. The > takes the output and puts it in a file – in this case connections.txt.
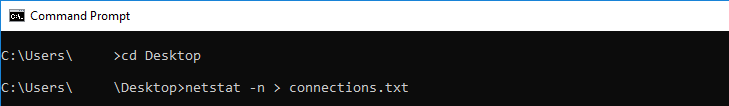
Since we’re sending the output to a file, you won’t see any on-screen output when you press enter.
Manipulating the data with Microsoft Excel
Quickly open connections.txt to ensure the output is correct. Then, to make it easier to manipulate, open it in Microsoft Excel (or another spreadsheet program), delete the top four rows, and use Data > Text to Columns to convert the ouput into a table using spaces as delimiters.
When Excel has done its magic, the data should be split neatly into columns like this:
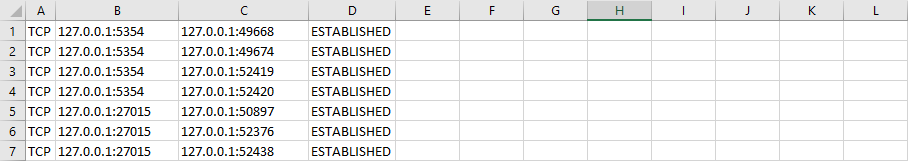
Next we need to narrow this data down to a list of external IP addresses that the computer is connected to. Delete any rows where the foreign IP is the loopback address (127.0.0.1), and then delete all columns except Foreign Address (in my case that’s column C). Now we need to separate out the IP addresses and ports by entering the following formula in the newly empty column B:
=LEFT(A1,FIND(":",A1&":")-1)This will find everything before the first colon (i.e. the one separating the IP address and the port number) and return it in the cell in column B. Copy this formula into every cell in column B, copy the entire column, use Paste Special (Ctrl + Alt + V) to paste the values into column A and use Remove Duplicates to get rid of copies of any addresses the PC was connected to on multiple ports.
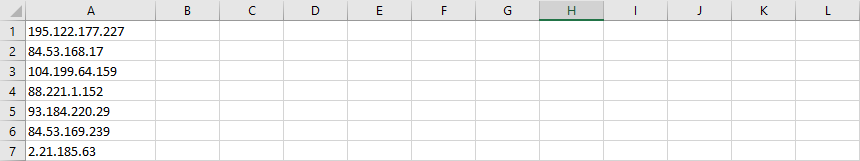
You should now be left with a list of unique destination IP addresses like the one above.
Gathering information on the IP addresses
Now for the simple bit – finding out which countries and organisations the IP addresses belong to – and the not so simple bit – trying to work out whether they’re potentially malicious.
Copy your list of destination IP addresses and paste them into a bulk IP WHOIS lookup tool like the one at InfoByIP.com. Hit Lookup, wait a moment, and you’ll get output like this:
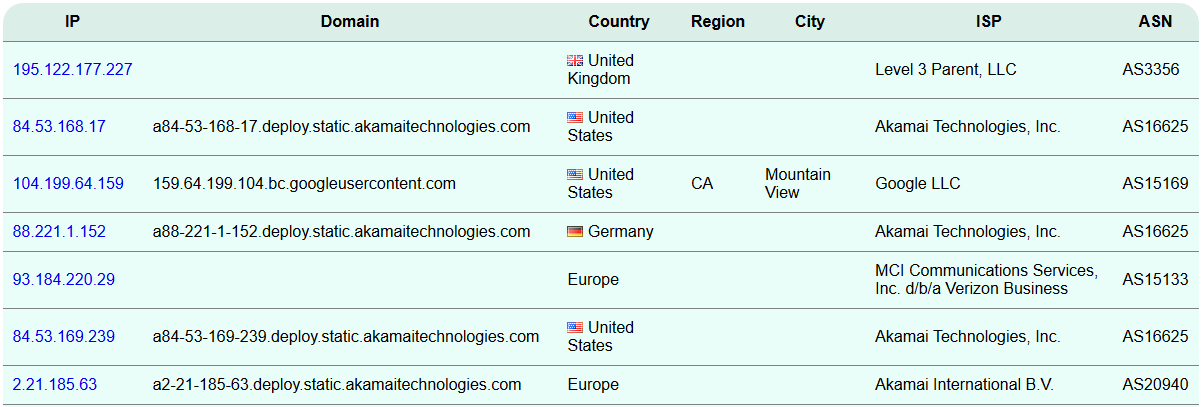
Hopefully, most of the IP addresses the system was communicating with are expected and belong to well-known companies – Google, Microsoft, and Amazon, for example. But if there are any you don’t understand, there are a few steps you can take to investigate them.
Investigating suspicious connections
First, we can do a bit more digging on the IP address and any open-source intelligence (OSINT) associated with it. A Google search can sometimes return some information, but for more reliable data try searching in the IBM X-Force Exchange, which will give you a risk score along with details of any malicious activity others have noted associated with the address (e.g. botnet activity, spam campaigns).
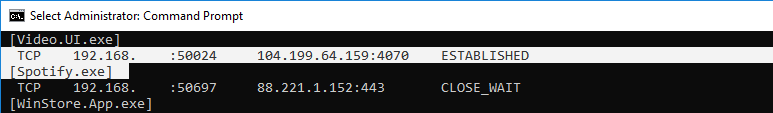
If you refer back to the original netstat output, you can also do some searching around the port the connection used. This won’t help much if it was on port 80 or 443, but it can sometimes shed some light on the connection’s nature – for example, a quick search shows port 4070 is associated with Spotify.
Finally, starting Command Prompt as an administrator and running netstat with the -b argument will attempt to show the applications associated with each connection. In this case, I can confirm that the connection out on port 4070 is indeed associated with Spotify.exe.
There’s much more that can be done to investigate IP addresses and connections, of course, and much of the process described above could be automated with Python, but perhaps those are blog posts for another day. I hope the process above is helpful – if you have any more tips on analysing connections from a host then leave a comment below and let me know!
Photo from Pixabay

