Automatically generating SOC emails with a Python script

The life of a SOC analyst – as is the case with many other jobs – can involve a lot of repetitive tasks, including the process of writing tens of similar emails each day. But what if this could be automated, saving time and reducing the potential for error?
The email template
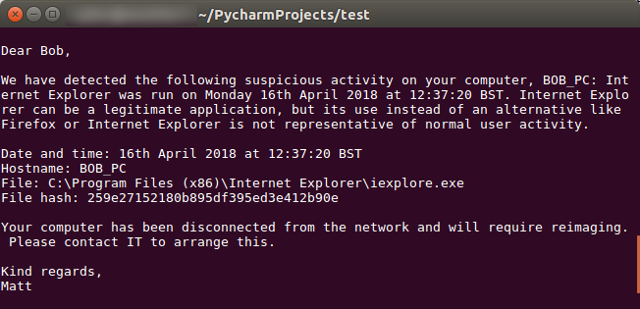
The most common email that a cyber security analyst has to send is to tell someone that there’s something wrong with their computer. The template looks something like this:
Dear Bob,
We have detected the following suspicious activity on your computer, BOB_PC: Internet Explorer was run on Monday 16th April 2018 at 12:37:20 BST. Internet Explorer can be a legitimate application, but its use instead of an alternative like Firefox or Internet Explorer is not representative of normal user activity.
Date and time: 16th April 2018 at 12:37:20 BST
Hostname: BOB_PC
File: C:\Program Files (x86)\Internet Explorer\iexplore.exe
File hash: 259e27152180b895df395ed3e412b90eYour computer has been disconnected from the network and will require reimaging. Please contact IT to arrange this.
Kind regards,
Matt
It’s a simple enough format, but when sending many of these each day (or even several at the same time) all that copying and pasting can take a while and lead to errors. What if I change the hostname in the list of technical details but forget to change it in the first sentence, for example? Some simple Python, involving little more than input prompts and variables, can help. Here’s how it works…
Getting information from the user
First, let’s get the details we need from our SOC analyst. In this case, the email template includes the user’s name, the hostname, a description of the activity, the date and time it was detected, the file involved, and the file hash. To add a little complexity, let’s also assume there’s another possible scenario where the analyst is just asking for information.
user_name = raw_input(“User name: “)
detection_hostname = raw_input(“Hostname: “)
detection_description = raw_input(“We detected… “)
detection_date = raw_input(“Detection date: “)
detection_time = raw_input(“Detection time: “)
detection_file = raw_input(“File path: “)
detection_hash = raw_input(“File hash: “)
disconnected = raw_input(“Disconnected? (Y/N): “)
Setting up the message template
Now the analyst has entered the necessary information, let’s establish the template and insert those variables. If your SOC has more than one email template then you could build in a menu or prompt to ask the user to choose between them, but in this case I’m going to move forward with just the one to keep this walkthrough a bit simpler.
message_1 = (“Dear %s,” % user_name)
message_2 = (“We have detected the following suspicious activity on your computer, %s: %s” % (detection_hostname, detection_description))
message_3 = (“Date and time: %s at %s” % (detection_date, detection_time))
message_4 = (“Hostname: %s” % detection_hostname)
message_5 = (“File: %s” % detection_file)
message_6 = (“File hash: %s” % detection_hash)
message_7a = (“Your computer has been disconnected from the network and will require reimaging. Please contact IT to arrange this.”)
message_7b = (“Are you aware of this activity and do you know why it took place?”)
message_8 = (“Kind regards,”)
message_9 = (“Matt”)
Putting the pieces together
The final step is as simple as printing the relevant parts of the generated email to the screen (or a file, if you’d prefer) while using some simple logic to select the correct elements. To demonstrate how this works, I’ll use both the previous decision between disconnecting and questioning the user, and I’ll assume that our security tools don’t always give us a file hash.
print message_1
print message_2
print message_3
print message_4
print message_5if detection_hash == “”:
pass
else:
print message_6if disconnected == “Y” or disconnected == “y”:
print message_7a
else:
print message_7bprint message_8
print message_9
The hash line is only printed if a hash exists and the disconnection line is only printed if the analyst says the endpoint was disconnected. I’ve removed the empty print lines to save space here, but feel free to add some to give your message some neat spacing.
Output
The result is a nice, automatically generated message that can be copied and pasted into an email or a SOC tool. The automated process speeds things up and reduces the chances that the analyst will make an error when sending many emails each day.
Of course, this could all be taken a few steps further: the details of the detection could be pulled from a security tool API, for example, or the email could be automatically sent or fed to a SOC tool that would send it to the user. Perhaps I’ll look into that in a future post.
A note: I’m only just delving into the world of Python, and these posts are as much to get things straight in my own head as they are to show them to others. If anything looks wrong, or there’s a more efficient way of doing something, please let me know!
Photo from Pexels (CC0). Cropped.

